Take Care Before You Share Online
For starters, even in an open community of sharing, you should observe commonsense boundaries. As President Obama warned students in his September address to schools, “be careful what you post on Facebook
Don’t Lose Sight of Who Your Friends Are
When you write a Twitter
Recognize the Visibility of Your Posts
You’ve thought it through, and you want to shout to the world how you feel about having to work overtime and during a weekend that you had earmarked for recreational activities. You have checked and double checked, and you’ve determined that your boss is not in your network, so you let loose on the keyboard and speak your mind. Unfortunately, you’re not home free (figuratively speaking) just yet. Being outside of your network, your boss can’t see your post directly, but if a Facebook

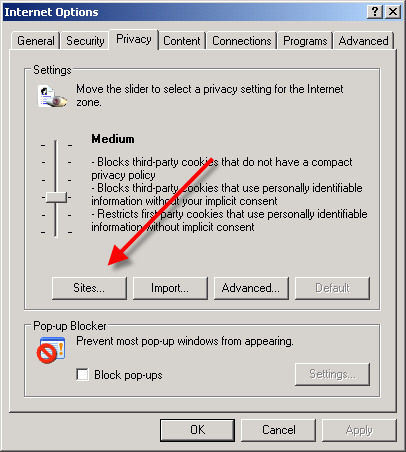
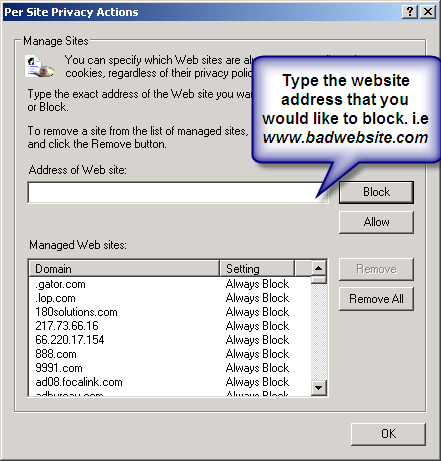
Define the Parameters of Your Privacy
Marrying privacy and social networking may seem terribly unintuitive. How can you be social and open, and yet protect your privacy? Well, just because you are choosing to share some information with a select group of people does not necessarily mean that you want to share everything with everyone, or that you are indifferent about whether the information you share is visible to all. Facebook, in particular, has drawn unwanted attention in connection with various privacy concerns. If you have used Facebook for a while, you may have noticed advertisements that incorporate your friends’ names or photos associated with them. Facebook does provide privacy controls for you to customize the types of information available to thirdparty applications. If you look at the Facebook Ads tab of the privacy controls, though, you’ll notice that it doesn’t give you any way to opt out of the internal Facebook Ads. Instead, it states (alarmingly) that “Facebook strives to create relevant and interesting advertisements to you and your friends.”
Approach Tattletale Quizzes With Caution
For many users, one of the primary attractions of Facebook
Facebook Policy Concerns in Canada
Facebook’s privacy policies have run afoul of the Canadian government, too. Canada’s Privacy Commissioner has determined that those policies and practices violate Canadian privacy regulations, and has recommended various changes Facebook should make to comply with them. One of the commissioner’s biggest concerns involves the permanence of accounts and account data. Facebook offers users a way to disable or deactivate an account, but it doesn’t seem to provide a method for completely deleting an account. Photos and status updates might be available long after a user has shut down a Facebook profile. And like the ACLU, the Canadian government is unhappy about the amount of user information that Facebook shares with thirdparty application providers.

Exercise the Privacy Controls You Have
Although the concerns of the ACLU and the Canadian government run a little deeper, Facebook does offer privacy controls for restricting or denying access to information. Since Facebook is a social networking site designed for sharing information, many of the settings are open by default. It is up to you to access the Privacy Settings and configure the options as you see fit. For each available setting, you can choose to share information with Everyone, with My Networks and Friends, with Friends of Friends, or with Only Friends; if you prefer, you can customize the settings to finetune access further.

Beware of Hijacking and Phishing Scams
By its very nature, social networking is all about socializing, which means that users are more than usually disposed to let their guard down and share information. They come to the network to expand their professional connections, reestablish contact with old friends, and communicate in real time with pals and peers. And for predatory bad guys, launching social-engineering and phishing attacks in this convivial environment is like shooting fish in a barrel. Most people know not to respond to e-mail requests from exiled Nigerian royalty promising millions of dollars in return for help smuggling the money out of the country. (Anyone who doesn’t know better probably shouldn’t be on the Internet; such people are a danger to themselves and to others.) But what if a good friend from high school whom you haven’t seen in 18 years sends you a message on Facebook explaining how her wallet was stolen and her car broke down, and asks you to wire money to help her get home? You might be less suspicious than you should be. Attackers have figured out that family and friends are easy prey for sob stories of this type. Using other attacks or methods, they gain access to a Facebook account and hijack it. They change the password so that the legitimate owner can’t get back in, and then they proceed to reach out to the friends of the hijacked account and attempt to extort money such a Facebook message or e-mail plea, pick up the phone and call the person directly to confirm its legitimacy.
Don’t Let a Tiny URL Fool You
Another threat that has emerged recently as a result of social networking is the tiny-URL attack. Some URLs are very long and don’t work well in e-mail or in blog posts, creating a need for URLshortening services. In particular, Twitter, with its 140-character limit, has made the use of URL shortening services such as Bit.ly a virtual necessity. Unfortunately, attackers can exploit a shortened URL to lure users into accessing malicious Web sites. Since the shortened URL consists of a random collection of characters that are unrelated to the actual URL, users cannot easily determine whether it is legitimate or phony. TweetDeck, a very popular application for sending messages in Twitter, provides a ‘Show preview information for short URLs’ option, which offers some protection.
The preview window supplies details about the shortened URL, including the actual long URL that the link leads to. If you aren’t using TweetDeck for Twitter, or if you need to deal with shortened URLs on other sites and services, maintain a healthy dose of skepticism about what might lie behind the obfuscated address that a message points to.
Source: PC World